Data Store
| Predictable Pricing5 |
Threat hunting |
| Insightful results |
Threat hunting |
IBM QRadar Data Store enables organizations to cost-effectively collect, parse and store large volumes of security and IT operations data.
![]() Build a cost-effective data lake
Build a cost-effective data lake
Collect, parse and store log data throughout the organization at a fixed and predictable price.
![]() Share data between Security and IT Ops
Share data between Security and IT Ops
Centralize enterprise-wide data for reporting and analytics, and control access to data based on data type and user role.
 See more during AI-driven investigations
See more during AI-driven investigations
Provide QRadar Advisor with Watson with a much broader set of local data to mine so that it can generate even deeper insights into threats within your environment.
 Address custom use cases
Address custom use cases
Leverage the QRadar SDK to build custom apps and analytics on top of your data to address a variety of unique security and IT operations use cases.
![]() Confidently manage compliance
Confidently manage compliance
Store a wide range of data for a prolonged period of time to help cover regulatory and audit questions that may arise in the future.
 Gain a starting point for threat hunting
Gain a starting point for threat hunting
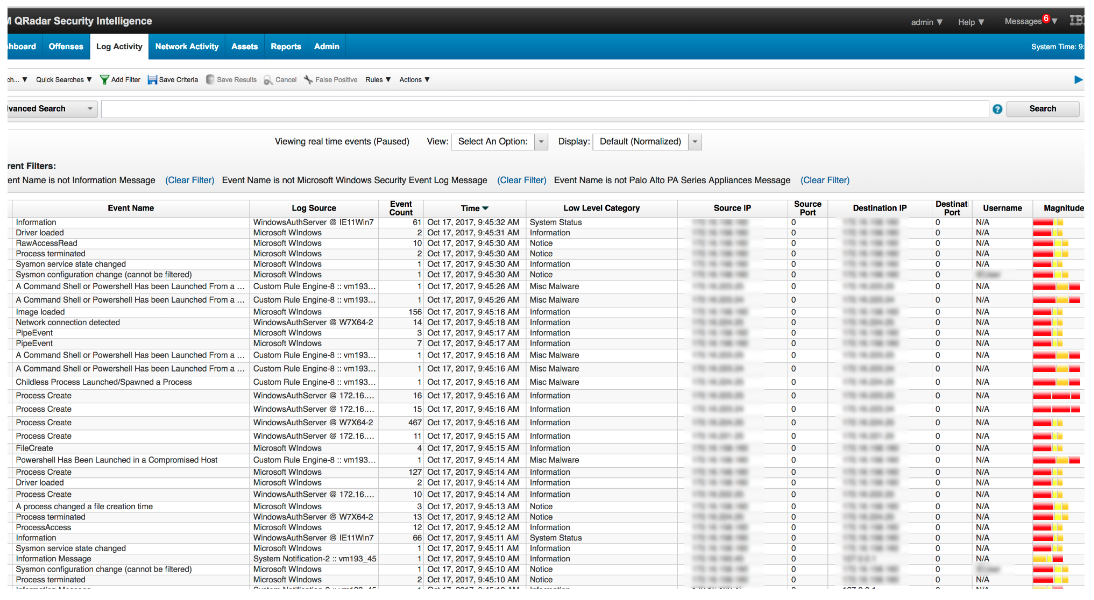
Provide security teams with massive volumes of data to which they can pose a variety of questions via Ariel Query Language and easily filter through results.
Better manage compliance
Problem
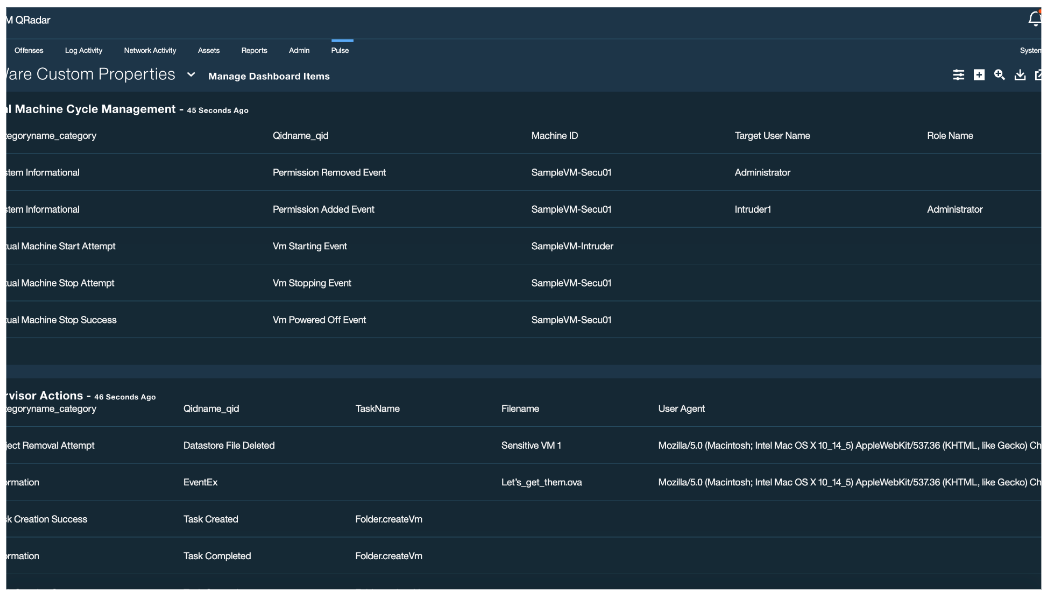
Siloed data coupled with exponentially increasing costs of long-term data retention make it difficult to effectively address compliance.
Solution
Save non-critical security data and IT logs directly to storage at a cost-effective, predictable price. Retain the data as long as needed, and easily run reports directly from one centralized console to help demonstrate compliance.
Enable proactive threat hunting
Problem
Threat hunting requires a massive amount of data so that hunters can pose questions and easily pivot without reaching self-inflicted dead ends. Often, the prohibitive cost of data retention limits security teams' abilities to start threat hunting.
Solution
Cost effectively store as much data as needed and provide threat hunters with centralized search tools so they can effectively build a log data lake and gain meaningful threat insights from that data lake.
References might include unofficial support. Prior to that reason without any control of the referencing contents. It might not be the most reliable source.
All references are not official. Ingram Micro (China) Limited All rights reserved
Please select one